Artificial Intelligence for Base and Facility Security: Intelligent Systems for Protection, Prediction, and Response
Artificial Intelligence for Base and Facility Security: Intelligent Systems for Protection, Prediction, and Response
By Ronen Kolton Yehuda (Messiah King RKY), June 2025
Abstract
As security threats evolve—ranging from terrorism and sabotage to drone attacks, insider threats, and cyber-infiltration—securing physical spaces like military bases, energy facilities, airports, and command centers requires more than walls and cameras. Artificial Intelligence (AI) enables a shift from static defense to dynamic, real-time security ecosystems. This article introduces a framework for using AI to protect locations and installations through multi-sensor fusion, resource allocation, autonomous alerting, incident scripting, and spatial analysis. The article includes technical components, ethical requirements, deployment strategies, and use-case scenarios.
1. Introduction: The Need for AI-Enhanced Security
Critical infrastructure and high-risk zones (military bases, airfields, government centers, factories) require more than human guards and passive systems. AI enhances these by providing:
Predictive threat modeling
Real-time sensor integration
Automated threat classification
Incident response scripts and playbooks
Intelligent deployment of patrols, drones, and reinforcements
AI doesn’t replace human security—it amplifies it with constant vigilance and logic-driven action, even under stress or chaos.
2. System Architecture Overview
Module Function
Sensor Fusion Engine Merges data from CCTV, radar, thermal, acoustic, and environmental sensors
Threat Detection AI Identifies suspicious movements, masked individuals, drones, weapons
Location Risk Evaluator Analyzes terrain, surrounding zones, and recent patterns
Resource Recommendation AI Suggests placement of guards, towers, drones, and emergency assets
Incident Script Engine Generates if-then-response protocols for different threat levels
Ethics and Compliance Core Ensures AI behavior stays within law and command restrictions
3. Intelligent Site Security: From Surveillance to Prediction
3.1 Real-Time Surveillance and Tracking
AI connects to a grid of security cameras, motion sensors, and biometric scanners to monitor base perimeters, entrances, internal zones, and access points. Computer vision and thermal imaging flag anomalies such as:
Masked individuals in off-limits zones
Loitering near sensitive installations
Unusual vehicle behavior at gates
Sudden drops in visibility due to smoke or fog
3.2 Pattern Recognition and Behavioral Anomalies
AI learns regular patterns—daily vehicle flows, shift changes, environmental baselines—and flags deviations. Example triggers:
Movement in an off-limits hangar at 3 AM
A person pacing near a fuel depot
Drone hovering beyond normal height thresholds
4. AI-Based Resource Placement and Recommendations
4.1 Guard and Patrol Optimization
AI evaluates blind spots, threat levels, access logs, and incidents to recommend optimal:
Patrol routes (adjustable in real-time)
Guard post placement
Drone hover zones
Example Output:
"Increase drone surveillance at Northwest perimeter between 02:00–04:00 due to repeat sensor anomalies in adjacent civilian area."
4.2 Emergency Resource Allocation
In the event of expected or unfolding threats, AI preemptively stages:
Firefighting units near fuel storages during heatwaves
Medical units near open-air events
Communication relays in blackout-prone sectors
5. Location Analysis and Strategic Placement Recommendations
AI evaluates security risk factors when choosing or reinforcing a site:
Factor AI Evaluation Parameters
Terrain Line-of-sight for guards, elevation for towers or radars
Proximity to Threat Zones Civil unrest, enemy lines, known smuggling corridors
Infrastructure Access Roads, power, communication lines (and redundancy plans)
Historical Threat Data Past sabotage, intrusion, or drone activity patterns
Civilian Proximity Balance between protection and avoiding population collateral
Output
Output Example:
“Suggested relocation of ammo storage 300m north: reduces crossfire risk to adjacent village by 90% and improves drone detectability.”
6. Incident Script Engine: Real-Time Action Protocols
AI generates dynamic incident scripts based on type, intensity, and location of the threat.
Example Script – Intruder at Perimeter Fence
{
"incident_id": "intruder_perimeter_0230",
"detection": "thermal_camera_E3, motion_sensor_E2",
"confidence": "92%",
"steps": [
{"action": "alert_nearby_patrol", "priority": "high"},
{"action": "activate_spotlight_E3", "duration": "10s"},
{"action": "send_drone", "drone_id": "DRN7"},
{"action": "log_event", "timestamp": "02:31:04"},
{"action": "initiate_voice_warning", "language": "multi"}
]
}
Example Script – Suspicious Vehicle at Entrance
Scan license plate + compare to whitelist
Alert gate guard + display risk rating
Activate barrier and wait for human confirmation
7. Use Cases and Deployment Scenarios
Scenario Description
Military Base Full perimeter defense, drone patrols, internal access control, alerts
Nuclear Facility Radiation monitoring + AI-based breach detection + insider behavior modeling
Forward Operating Base AI-predictive IED risk zones, counter-sniper drones, low-bandwidth operations
Civil Infrastructure Airport perimeter detection, anomaly alerts, crowd flow AI
Embassy Security VIP access monitoring, protest detection, de-escalation AI
8. Ethical and Legal Safeguards
No Lethal Action Without Human Confirmation
All autonomous responses are non-lethal unless explicitly authorized by command.Privacy-by-Design
Civilian faces blurred/stored only with authorized triggers. Logs encrypted.Bias Detection
AI must not discriminate based on race, attire, or non-threatening behavior. Continuous retraining is mandatory.Override Protocols
Human commanders have live dashboard access and override capability for every AI script.
9. Integration with Defense and Civil Systems
AI security platforms can integrate with:
National defense radar grids
Emergency response dispatch
Smart city traffic and energy systems
Civilian drone traffic control
Secure mobile command apps
10. Conclusion
Artificial Intelligence is no longer just a camera-enhancer—it is the silent logic layer behind a secure base or facility. By predicting threats, placing resources wisely, and guiding every action script with human oversight, AI becomes a guardian—not just a watcher.
Its future includes:
Distributed AI defense nodes
Inter-base predictive coordination
Simulated drills using AI-generated threats
Real-time ethical compliance audits
The smarter our infrastructure becomes, the more it must be secured—not with walls, but with intelligent and moral systems.
Keywords
AI base security, autonomous defense, intelligent surveillance, incident scripting, ethical AI systems, patrol optimization, AI-powered threat detection, military infrastructure security, base protection AI, drone defense coordination
Technical Framework: Artificial Intelligence for Base and Facility Security
By Ronen Kolton Yehuda (Messiah King RKY) – June 2025
Abstract
This technical paper presents a modular AI architecture for autonomous and semi-autonomous security of physical locations, including military bases, airports, critical infrastructure, and command centers. It details sensor fusion, threat detection, resource recommendation, incident response scripting, and human-in-the-loop control layers. The system is designed to preempt, monitor, and mitigate security risks through dynamic behavior analysis, real-time environment scanning, and programmable compliance enforcement. Deployment options include fixed, mobile, and distributed node configurations.
1. System Objective
To secure high-value or high-risk physical locations using a multi-layered AI framework capable of:
Multi-modal threat detection (visual, thermal, audio, radar, etc.)
Resource deployment optimization
Real-time incident scripting
Adaptive patrol path generation
AI-assisted human decision support
Auditable ethical compliance and override
2. System Architecture Overview
Layer Components Purpose
Sensor Fusion Layer Visual (CCTV), IR, LIDAR, radar, acoustic, motion Data aggregation and anomaly detection
Threat Analysis Engine Object tracking, gait analysis, loitering models Behavior-based risk classification
Resource Optimization AI Spatial grid + asset positioning engine Patrol, guard, drone, camera placement recommendation
Incident Script Generator Rule-based + AI-generated protocols Predefined and dynamic response sequences
Location Risk Evaluator GIS + urban/terrain logic Base siting, blind spot mapping, environmental scoring
Ethics Filter Rule of Law models, override logs, geofencing Ensure legal compliance and enforce red-line constraints
Operator Interface Secure dashboard, manual override, alerts UI Human command integration
3. Sensor Fusion & Threat Detection
3.1 Multi-Modal Sensor Grid
Inputs are processed through time-synced modules using cross-validation.
Visual AI: Object detection, intrusion detection, facial recognition
Thermal Mapping: Human/animal detection through heat gradients
Motion Tracking: Speed, direction, proximity alerts
Acoustic Signatures: Gunfire, engine noise, abnormal speech patterns
Drone Radar: Detects low-flying rotary-wing or fixed-wing drones
3.2 Threat Classification Models
Deep CNN + LSTM pipelines to track motion patterns
Mask Detection, posture anomaly filters (e.g., crouching + static = high threat)
Re-ID (Re-identification) models to track individuals across camera zones
Confidence scoring system for multi-sensor corroboration
E.g., Thermal + Motion + Loitering Pattern = High Probability Intrusion (0.91)
4. Resource Allocation and Placement Optimization
4.1 Spatial Grid Modeling
The facility is divided into zones (Z1…Zn) based on:
Entry points, terrain elevation, lighting, historical incidents
Real-time risk level matrix:
R(Zi) = f(threat_density, visibility_score, critical_asset_proximity, historical_risk)
4.2 Optimization Function
Let G = set of guards, D = set of drones, C = camera assets.
Goal: Maximize coverage and response time, minimize risk exposure
Objective:
maximize ∑ (Coverage(Zi) × Priority(Zi)) - ∑ (Deployment_Cost)
subject to:
ResponseTime(Zi) ≤ T_threshold
G_total ≤ budget_guard
D_total ≤ drone_capacity
5. Incident Script Engine
5.1 Script Format (Example JSON)
{
"incident_id": "intrusion_fence_E4",
"timestamp": "2025-06-14T03:47:11Z",
"confidence": 0.93,
"threat_type": "human_intruder",
"response_steps": [
{"action": "alert_security_ops", "mode": "priority"},
{"action": "deploy_drone", "drone_id": "D-03"},
{"action": "activate_spotlight", "zone": "E4"},
{"action": "broadcast_warning", "language": ["en", "ar", "he"]},
{"action": "log_event", "persistence": "permanent"}
],
"ethics_check": "passed",
"override_possible": true
}
5.2 AI-Generated vs. Predefined Protocols
Predefined = curated responses to common scenarios
AI-Generated = built from NLP + real-time asset capacity + outcome optimization
Uses sequence-to-sequence transformer models to generate complex multi-stage responses
6. Location Risk Scoring Framework
Factors and Input Sources:
Risk Dimension Parameters
Terrain Vulnerability Elevation, natural cover, visibility, escape paths
Surrounding Environment Civilian proximity, slum adjacency, protest hotspots
Historical Incident Map Past attacks, thefts, breaches, drone violations
External Influence Zones Terrorist presence, smuggling routes, hostile surveillance
Risk Score per Location =
R = w1*T + w2*S + w3*H + w4*E
where:
T = terrain exposure
S = social-political tension
H = historical events (weighted by recency)
E = external intelligence sources
7. Human-AI Interaction and Ethical Guardrails
7.1 Human-in-the-Loop (HITL)
All lethal or detainment actions require human review unless under autonomous protocol pre-approval
Every action is logged with:
initiator,response_type,timestamp,ethics_passed,commander_override
7.2 Red-Line Filters
Geo-fenced civilian zones (schools, mosques, clinics) tagged as No-Engage
Face/attire recognition excludes medical staff, surrendered individuals
Response suggestions filtered by:
Collateral risk matrix
IHL (International Humanitarian Law) compliance ruleset
8. Deployment Models
Type Power Source Use Case Examples
Fixed Command Hub Grid / Microgrid HQ, airport, nuclear plant Full-stack AI + human teams
Edge Unit Node Battery + Solar Border bases, outposts Local sensor + alert logic
Drone Swarm Net Fuel-cell / Li-ion Rapid perimeter + supply patrols Autonomous aerial response
Mobile Security Kit Hybrid Battery Events, VIP security, convoy Rugged portable deployable
9. Integration and Protocols
Data Sync: All nodes sync to Central Threat Cloud (encrypted, decentralized)
Communication: Mesh network using adaptive frequency hopping (jam-resistant)
APIs:
GET /incidents/todayPOST /deployments/newPATCH /risk-map/{zone_id}
Sim Mode: Run simulations using historical + synthetic data for training
10. Future Enhancements
AI-generated training missions with synthetic enemy actors
Psychological risk evaluation: facial fatigue, stress detection
Crowd anomaly mapping during mass gatherings
Inter-base coordination via swarm-AI threat intelligence relay
Ethical Escalation Protocols (EEP) embedded into every decision branch
Conclusion
AI-powered facility and base security must combine precision, speed, and restraint. This system presents a scalable, ethically bound architecture for real-world deployment in critical environments. By fusing advanced sensing, scenario modeling, and legal logic enforcement, this AI platform offers not just smarter security—but security that honors safety, law, and humanity.
Keywords
AI facility defense, AI security grid, autonomous patrol, military base protection, ethical AI systems, drone surveillance AI, anomaly detection, tactical scripting, red-line enforcement AI, intelligent infrastructure defense
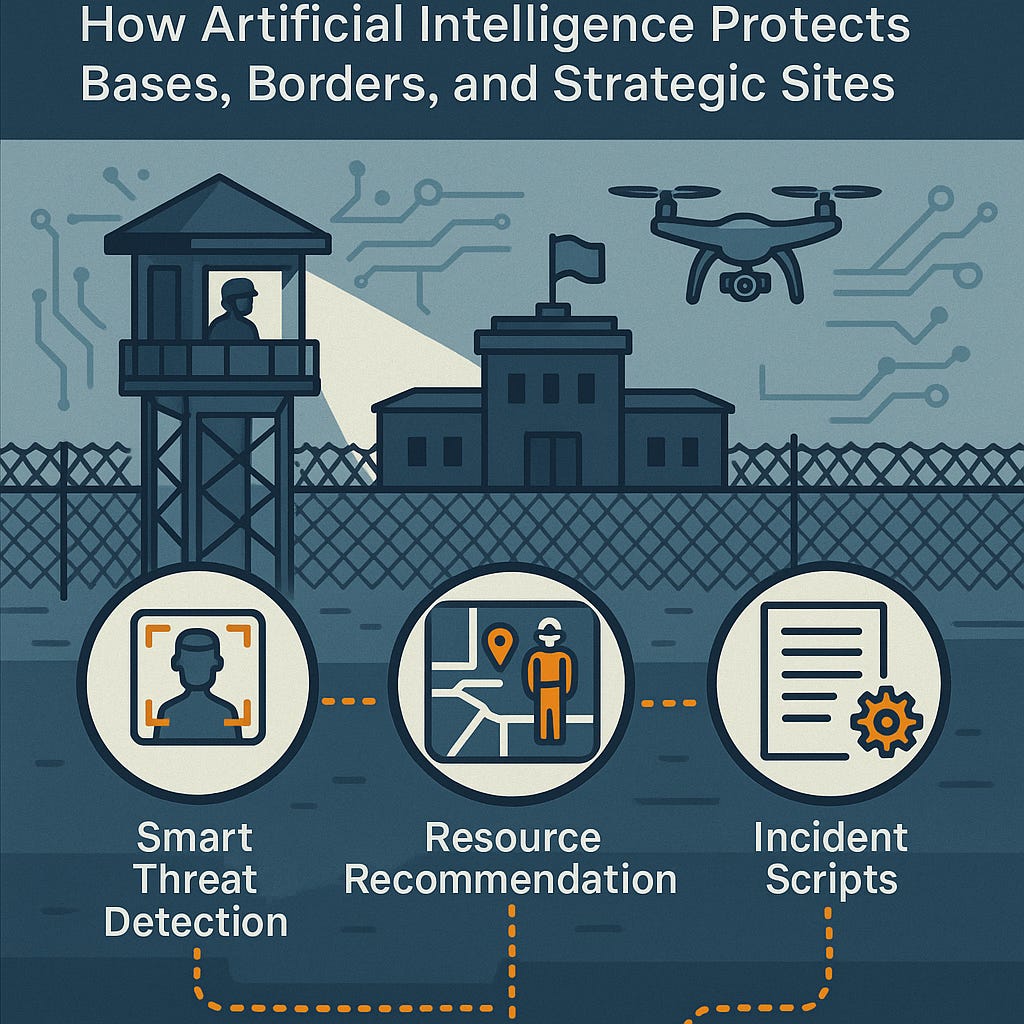
🛡️ AI for Facility Security: How Artificial Intelligence Protects Bases, Borders, and Strategic Sites
By Ronen Kolton Yehuda (Messiah King RKY)
June 2025
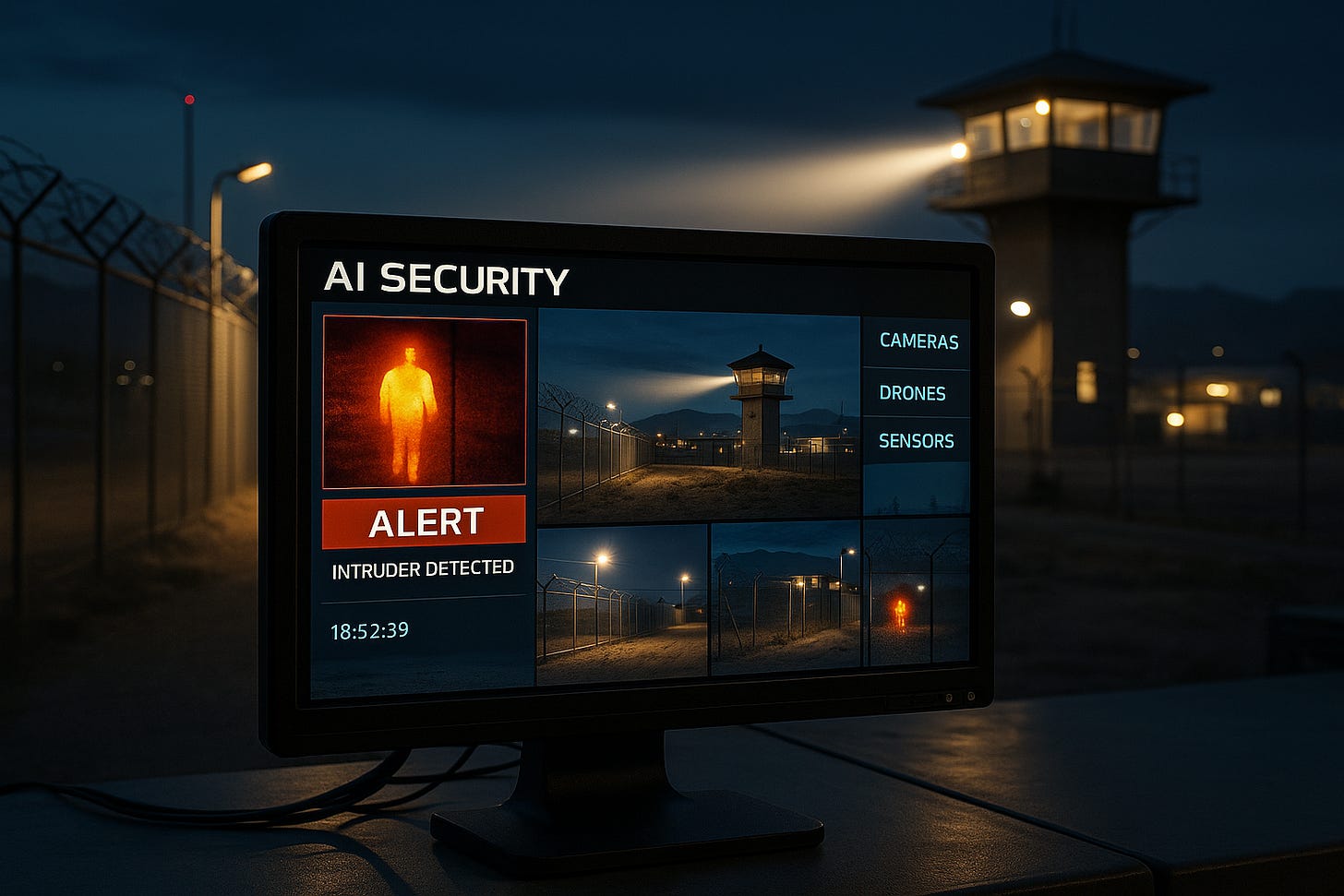
In an era of advanced threats—from drones and intrusions to cyberattacks and sabotage—protecting physical locations such as military bases, power stations, airports, and borders has never been more complex. Cameras and fences are no longer enough. What’s needed now is intelligence—Artificial Intelligence.
AI is revolutionizing security operations by turning ordinary surveillance into predictive, responsive, and ethical protection systems. This article explores how AI can be used to protect strategic locations, how it decides where to send resources, and how it reacts to incidents in real time—without losing human oversight.
🔍 What Is AI Security for a Place?
AI security refers to systems that can watch, detect, analyze, and respond to threats automatically or semi-automatically. These systems combine video feeds, sensors, maps, and behavior detection software into one intelligent brain that watches over a facility—day and night.
Instead of just recording what happened, AI systems predict what might happen next.
🧠 Key Capabilities of AI Facility Protection
1. Smart Threat Detection
AI scans video, motion, and thermal sensors to detect intrusions or suspicious behavior—like someone lingering too long near a fence, or a drone flying where it shouldn’t.
It can recognize faces, identify weapons, detect loitering, and even spot crawling or crouching movements that human guards might miss.
2. Resource Recommendation
AI doesn’t just watch—it helps command. It recommends where to place cameras, when to deploy patrols, or how many guards are needed at each location based on historical data and real-time risks.
For example:
“If Zone C has had 3 breach attempts in 2 weeks, suggest increasing drone patrols and spotlight coverage.”
3. Incident Scripts
When something happens—like a break-in, drone attack, or perimeter breach—AI generates a script of actions, such as:
Alert security
Activate sirens or lights
Send drones to the area
Notify nearby forces
Broadcast warnings in multiple languages
Each step is chosen based on the type of threat, available personnel, time of day, and legal limitations.
🗺️ How Does AI Choose the Best Location for Resources?
Using a digital map of the base or facility, AI assigns scores to each zone based on:
How visible and accessible it is
Proximity to sensitive assets (like weapon storage or servers)
History of past incidents
Political or social risks in the area
Based on these scores, AI suggests the most effective layout for guards, cameras, floodlights, and even walls or drone patrol routes.
📜 Example of an AI Security Script
Scenario: Intruder detected on thermal camera near perimeter fence (Zone E4)
AI Response Script:
Raise alert to central command
Flash perimeter lights in Zone E4
Send two aerial drones for overhead visual
Broadcast warning via loudspeaker in 3 languages
Record event and trigger review mode
If intruder moves toward critical area, notify rapid response team
All actions are logged and include a human override option if needed.
🧩 Ethics and Oversight
AI does not replace human responsibility. Every action—especially if it involves force or confrontation—goes through:
Human-in-the-loop review for approval
No-kill zones for schools, clinics, and civilian zones
Facial recognition safeguards to avoid misidentifying civilians or workers
Red line filters to automatically reject illegal or immoral responses
Every step taken by the system is auditable and transparent.
🚀 Where Can AI Facility Security Be Used?
AI security systems are already being designed or deployed in:
Military bases (border outposts, airfields, naval yards)
Critical infrastructure (power plants, data centers)
Airports and seaports
High-risk government buildings
Temporary field bases and disaster zones
VIP convoys and large event protection
Systems can be installed permanently or used as mobile kits powered by batteries and solar panels.
🌍 The Future of Secure Facilities
AI is not just watching—it’s learning. Future upgrades will include:
Crowd behavior prediction during protests or emergencies
Emotional detection (like fear or aggression) from facial cues
AI security coordination between multiple bases in a region
Simulated training with fake threats to test system response
AI-led de-escalation tactics for peacekeeping missions
The vision: smart, ethical, fast-acting protection that adapts without relying only on muscle or firepower.
🧭 Final Thoughts
Securing a place today is about more than walls and weapons. It’s about awareness, speed, and control. With AI, we can protect people and property with intelligence—predicting threats, responding wisely, and always staying within the law.
When designed with humanity in mind, AI doesn’t just guard—it guides. It becomes a partner in keeping our most important locations safe, efficient, and ethical.
Keywords:
AI facility protection, intelligent base security, automated threat detection, AI patrol systems, smart incident scripts, AI in defense infrastructure, ethical AI security, drone surveillance, base automation, intelligent guard systems
24/7 AI Security for Facilities and Bases: Real-Time Protection with Smart Alert Systems
By Ronen Kolton Yehuda (Messiah King RKY), June 2025
Abstract
In an era of continuous threat exposure, from drone incursions to insider sabotage, security must be both constant and intelligent. Artificial Intelligence (AI) offers around-the-clock protection that goes beyond passive surveillance, enabling real-time alerts, autonomous analysis, and fast decision support. This article introduces the concept of 24/7 AI Security for strategic facilities—focusing on how AI-driven systems ensure full-time vigilance, threat classification, and instant response coordination.
1. Introduction: Why 24/7 AI Security Is Essential
Human guards need sleep. Cameras need monitoring. But threats can emerge at any moment—especially during the off-hours. Traditional security systems often detect incidents after they occur. AI security systems operate continuously, analyzing multiple input streams without fatigue, bias, or delay.
24/7 AI security enables:
Instant recognition of intrusion or tampering attempts
Automated alerts to on-site or remote operators
Preemptive deployment of drones or smart barriers
Legal and ethical response enforcement
2. Core Components of a 24/7 AI Security System
Module Role Sensor Fusion Engine Unifies data from cameras, thermal sensors, acoustic monitors, drones Threat Intelligence Core Evaluates activity patterns, compares against normal baselines Real-Time Alert Engine Pushes alerts to mobile, desktop, or control systems instantly Incident Playbook AI Generates pre-scripted response protocols for various threats Human Oversight Interface Allows command center staff to review, override, or escalate
3. Real-Time Alert Logic
AI systems process data as it streams in—detecting, verifying, and responding within milliseconds. Alert workflows typically follow this path:
Detection – anomaly flagged (e.g., heat signature on perimeter fence)
Validation – AI cross-checks with known events or authorized personnel
Alert – if suspicious, a real-time alert is pushed to:
Mobile command apps
Security consoles
Drones and patrols
Escalation Protocol – if threat confirmed, multi-step responses begin
Example Real-Time Alert:
{
"alert_id": "Z3_perimeter_intrusion_0345",
"confidence_score": 0.96,
"location": "Zone 3 North Fence",
"detected_by": ["thermal_cam_T3", "motion_sensor_M7"],
"recommended_response": ["dispatch_drone", "activate_lights", "alert_operator"],
"timestamp": "2025-06-14T03:45:12Z"
}
4. 24/7 Surveillance Without Blind Spots
AI constantly monitors:
Perimeters with object detection and loitering analysis
Entrances with facial recognition, badge validation, and gait analysis
Airspace using drone-tracking radar and geo-fence violation alerts
Sensitive zones with temperature, noise, and vibration tracking
Shift changes and nighttime operations are not weaknesses in an AI-based system. It learns when fewer humans are present and compensates with tighter watch zones.
5. Autonomous Response and Human Review
AI doesn’t act alone—it works in coordination with human oversight. When a high-confidence threat is detected:
Automated actions begin (lights, sirens, voice warnings, drone dispatch)
Operator receives alert and may:
Confirm and escalate
Override for known personnel
Log as false alarm (training data is updated)
AI can handle 99% of low-tier events autonomously, allowing humans to focus on complex decisions.
6. Applications of 24/7 AI Security
Location Type AI Use Cases Military Bases Patrol automation, intrusion detection, drone tracking Energy Facilities Sabotage prevention, fire risk alerts, vibration sensors Airports Gate security, perimeter breaches, crowd flow monitoring Government Sites Unauthorized access detection, VIP movement tracking Border Checkpoints Vehicle scanning, document verification, loitering analysis
7. Benefits Over Traditional Security Systems
Traditional 24/7 AI-Based Passive cameras Active behavior analysis Slow manual alerts Instant mobile alerts Human fatigue Non-stop attention Routine patrols Dynamic, optimized patrols Delayed response Pre-scripted rapid reactions
8. Ethical and Operational Safeguards
Even under full automation, ethics and legality remain central:
No lethal action without human approval
Privacy-by-design: facial data stored only when needed
Override access: command staff can pause, override, or disable any script
Audit logs: every alert, action, and decision is logged with timestamps
9. Conclusion: Intelligence That Never Sleeps
AI security systems now serve as the digital eyes and ears of our most sensitive locations. With real-time detection, predictive insight, and scripted response—all monitored by human controllers—security becomes both smarter and safer.
By combining autonomous vigilance with human judgment, 24/7 AI security doesn’t just defend perimeters—it reshapes the future of infrastructure protection.
Keywords:
AI security, 24/7 monitoring, real-time threat detection, autonomous alerts, base protection, AI patrol, incident scripting, military AI, infrastructure defense, ethical AI security
⚖️ Legal Statement — Intellectual Property & Collaboration
Artificial Intelligence for Base and Facility Security: Intelligent Systems for Protection, Prediction, and Response
By Ronen Kolton Yehuda (MKR: Messiah King RKY)
June 2025
© 2025 Ronen Kolton Yehuda. All rights reserved.
This publication — including all derivative works, technical frameworks, articles, and system models titled under “Artificial Intelligence for Base and Facility Security,” “24/7 AI Security,” or related sections — constitutes the original intellectual property of Ronen Kolton Yehuda (MKR: Messiah King RKY).
It is protected under international copyright, patent, and moral rights law.
All described concepts, architectures, algorithms, terminology, and security frameworks — including sensor fusion systems, AI incident scripting, threat modeling logic, and ethical control structures — are considered proprietary inventions under the creative and research authorship of the Author.
Usage and Reproduction Rights
Permitted Use: Academic citation, brief quotation (up to 300 words), and non-commercial educational referencing — only with full attribution to Ronen Kolton Yehuda (MKR: Messiah King RKY).
Restricted Use: Any republication, reproduction, commercial adaptation, translation, AI-model training, or technical implementation based on the content requires prior written authorization from the Author.
Unauthorized use, including AI data extraction or derivative commercial deployment, is a direct infringement of intellectual property rights and may result in legal enforcement.
Collaboration & Licensing
Collaborators, partners, or organizations seeking to build upon or deploy any concepts presented herein must enter a formal written IP agreement with the Author.
Such agreement shall define authorship acknowledgment, ownership distribution, confidentiality, and ethical compliance obligations.
All co-developed works shall maintain attribution to the Author and cite the original framework title.
Ethical and Legal Responsibility
Given the dual-use and defense-related nature of this publication, all implementations, adaptations, or demonstrations of its principles must strictly comply with:
International Humanitarian Law (IHL)
Export control and sanctions regulations
Civilian protection and privacy statutes
Prohibition on lethal automation without human oversight
This publication is intended for academic, defense research, and ethical development purposes only. Any misuse or weaponization that violates humanitarian law is strictly forbidden and legally actionable.
Contact for Permissions and Collaboration
For licensing, institutional collaboration, research partnerships, or commercial proposals, please contact the Author directly through official or verified communication channels.
Ronen Kolton Yehuda (MKR: Messiah King RKY)
Founder, Author, and Intellectual Rights Holder
© 2025 – All Rights Reserved.
Authored by: Ronen Kolton Yehuda (MKR: Messiah King RKY)
Check out my blogs:
Substack: ronenkoltonyehuda.substack.com
Blogger: ronenkoltonyehuda.blogspot.com
Medium: medium.com/@ronenkoltonyehuda
Authored by: Ronen Kolton Yehuda (MKR: Messiah King RKY)
Check out my blogs:
Substack: ronenkoltonyehuda.substack.com
Blogger: ronenkoltonyehuda.blogspot.com
Medium: medium.com/@ronenkoltonyehuda