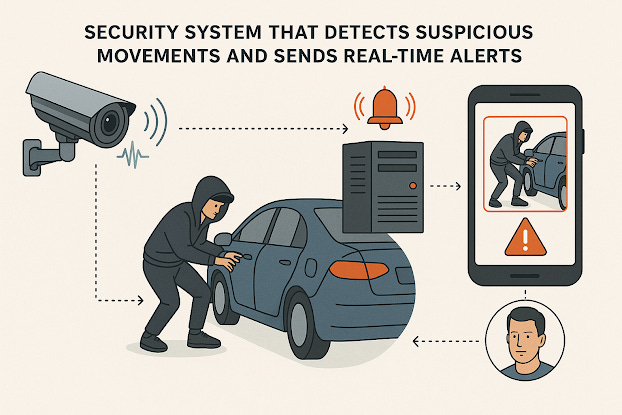
Security Software That Detects Suspicious Movements and Sends Real-Time Alerts / Integrated Surveillance Software for Real-Time Detection of Suspicious Movement and Sound
Title: Security Software That Detects Suspicious Movements and Sends Real-Time Alerts
Integrated Surveillance Software for Real-Time Detection of Suspicious Movement and Sound
Abstract
As global security challenges evolve, there is increasing demand for intelligent systems capable of real-time threat recognition and rapid alert delivery. This article presents the conceptual framework for an integrated security software system that monitors video and audio feeds to detect suspicious movement and abnormal sound patterns. The system uses artificial intelligence (AI) and machine learning (ML) to distinguish between routine environmental activity and events indicative of criminal intent, intrusion, or system sabotage. It is designed to operate across various environments including residential, vehicular, and commercial zones, with additional support for mobile and aerial surveillance platforms.
1. Introduction
Conventional surveillance systems rely heavily on manual monitoring and post-incident review. While effective in some scenarios, this reactive approach limits timely intervention. Emerging security threats—including theft, tampering, unauthorized access, and covert surveillance disruption—demand systems that not only monitor passively but also recognize and respond to danger as it occurs.
This article explores the design of a software-based security solution that integrates real-time video and sound analysis, dynamic notification protocols, and AI-powered recognition to enhance situational awareness and response capacity.
2. System Design and Architecture
2.1 Core Components
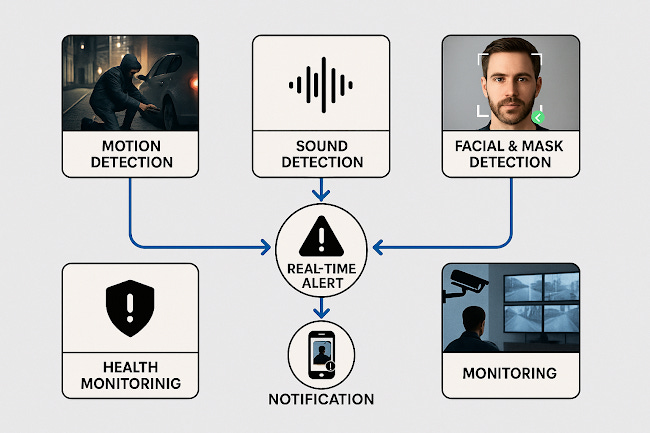
The proposed system architecture consists of modular components designed to manage motion, sound, user communication, and automated response:
Motion Detection Engine: Employs computer vision to track movement across camera feeds, distinguishing between routine and anomalous patterns (e.g., loitering, sudden acceleration, intrusion).
Acoustic Detection Module: Continuously monitors ambient sound for signatures such as glass breaking, raised voices, impact noise, gunfire, or explosions.
AI and Pattern Recognition Layer: Facilitates classification of both visual and audio events, supports facial recognition, and flags attempted obfuscation (e.g., the use of realistic silicone face masks).
Alert Management Subsystem: Constructs and dispatches multimedia alert packets (images, video, and/or audio) to designated users. Allows for parallel notification of multiple recipients.
Device and Health Monitoring Layer: Detects camera tampering, loss of connectivity, obstruction, or equipment damage.
Drone and Mobile Camera Interface: Integrates with remote or aerial surveillance units for flexible field coverage in complex environments.
3. Functional Capabilities
3.1 Real-Time Multimedia Alerts
Events are captured, logged, and sent to users as alerts. Each alert includes:
Timestamped images or video
Sound clips or waveform visualizations (if applicable)
Type of detected anomaly
Live-stream link for authorized escalation
3.2 Customizable Sensitivity
Users can configure detection thresholds to adapt to different environmental contexts or time periods, reducing false positives while maintaining a high level of vigilance.
3.3 Multi-User Notification and Role Assignment
The system supports simultaneous alert delivery to multiple users, which can include family members, security personnel, or administrators. User roles can be defined to limit or expand access privileges.
3.4 Facial Recognition and Anti-Mask Detection
Authorized individuals are stored in a local or encrypted cloud database. AI routines compare captured faces against the database and can detect mask anomalies based on thermal variation, movement inconsistency, or material irregularities.
3.5 Camera Health and Tamper Alerts
The system detects the following disruptions:
Camera is moved, tilted, or obstructed
Feed is cut off unexpectedly
Motion/audio analysis is disabled by external interference
3.6 Sound Event Classification
Audio recognition includes trained models for detecting:
Sudden impacts
Human distress
Breaking glass
Firearms and explosive discharge
Low-frequency tampering (e.g., lock picking or drilling)
4. Use Cases
ContextApplicationResidentialEntry detection, package theft prevention, backyard and garage monitoringVehicleProtection in parking zones, alerts during tampering, window break detectionCommercialOffice and storefront monitoring, after-hours surveillance, entryway controlPublic/InstitutionalTransportation hubs, parks, campuses, remote area observationIndustrialWarehouse perimeters, equipment tampering, shift-based threat analysis
5. Privacy and Ethical Considerations
The proposed system must comply with strict ethical and legal standards:
Data Ownership: All media and biometric data should be stored securely with full user control.
Facial Recognition Opt-In: Databases must be user-managed and clearly logged.
Exclusion Zones: Private areas (e.g., neighboring property) can be masked from detection algorithms.
Audit Trails: All activity within the system—alerts, data access, escalations—is recorded for transparency and accountability.
6. Scalability and Integration
The software is designed to scale from individual use to enterprise environments. Key compatibility includes:
Smart home ecosystems (e.g., locks, lighting, voice assistants)
Emergency communication platforms (e.g., police integration APIs)
IoT networks and cloud-based storage
Thermal and night-vision hardware for low-light applications
7. Limitations and Future Work
As a conceptual framework, the system faces several areas for future investigation:
Real-world deployment testing and false positive rate optimization
Broader sound dataset development for improved classification
Integration with biometric encryption and anonymized tracking
Enhanced AI model explainability and end-user transparency
Expansion to crowd analysis and anomaly detection at public events
8. Conclusion
The proposed surveillance software integrates motion and sound detection with AI-enhanced behavior recognition to deliver real-time threat identification. Its multi-modal alert system, compatibility with fixed and drone-based cameras, and capacity for user-defined configuration offer a flexible, scalable solution suitable for modern safety requirements.
This model represents a significant advancement in moving from passive monitoring to active security management—offering a platform that not only records but actively protects.
Title: Security Software That Detects Suspicious Movements and Sends Real-Time Alerts
Published originally at LinkedIn on: 2024-12-10 17:23
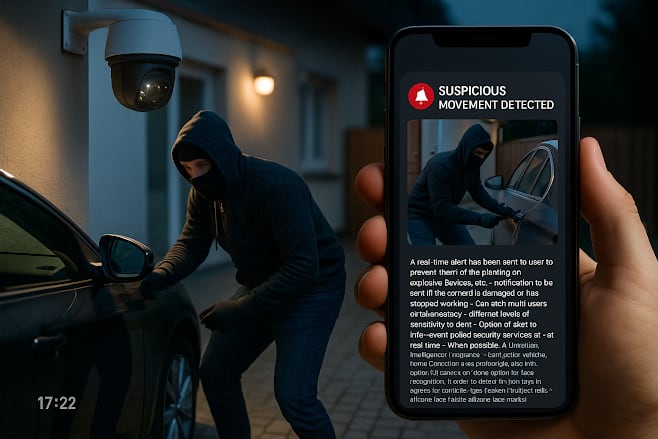
In an increasingly unpredictable world, enhanced surveillance and immediate alert systems are becoming essential for personal and public safety. This new security software concept is designed to detect suspicious movements near vehicles, homes, or secured areas through connected camera systems and to send instant alerts — including video or image captures — directly to users in real time.
The system is built to prevent incidents such as theft, tampering, unauthorized access, or even the planting of dangerous devices. It not only tracks motion but also identifies when a camera is damaged or goes offline, instantly notifying users of a potential breach in surveillance.
Key Capabilities Include:
Real-Time Alerts: Sends notifications with still images or short video clips whenever suspicious activity is detected.
Multi-User Notification: Allows alerts to be sent to multiple users at once — useful for families, security personnel, or business partners.
Customizable Sensitivity Levels: Users can set different levels of detection sensitivity, minimizing false alarms while optimizing threat detection.
Direct Security Response Options: Provides an option for users to share alert content with police or private security services at the moment of detection.
AI Integration (where applicable): When possible, AI is integrated to analyze behavior patterns and differentiate between harmless motion and potential threats.
Versatility Across Use Cases: Can be used for vehicle protection, home surveillance, or monitoring of specific locations or facilities.
Drone Camera Compatibility: Includes support for drones equipped with cameras, allowing aerial surveillance of larger or more complex areas.
Facial Recognition & Access Control: Recognizes familiar individuals with authorized access and alerts the user if unfamiliar faces or potentially realistic silicone masks are detected, signaling a possible disguise.
This solution brings together advanced motion detection, artificial intelligence, and user-friendly interfaces to deliver a robust defense system tailored to modern threats. Whether securing your car, your home, or sensitive public areas, this technology promises to provide peace of mind and proactive protection — all in real time.
How It Works:
The software operates in tandem with camera systems — fixed, mobile, or even drone-mounted — and is constantly analyzing input for suspicious movements, objects, or behavior. When triggered, the system captures the moment in high resolution and dispatches alerts to all connected users. These alerts can include:
Time-stamped video or photo snapshots
Camera health status (e.g., blocked, tampered, or offline)
Optional escalation tools such as instant police/security sharing
Through real-time connectivity, users can act quickly — preventing theft, trespassing, sabotage, or worse.
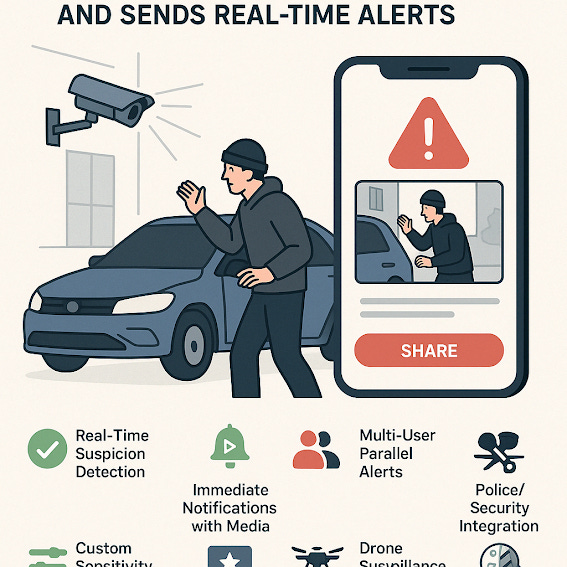
Core Features:
✅ Real-Time Suspicion Detection
Using motion tracking and behavior analysis, the system recognizes potential threats before they escalate.
✅ Immediate Notifications with Media
Each alert includes supporting visuals — ensuring users aren’t reacting blindly, but with clarity.
✅ Camera Health Monitoring
If a camera is disabled, damaged, or disconnected, the system immediately flags the issue.
✅ Multi-User Parallel Alerts
Supports multi-device and multi-user notifications, perfect for family members, building managers, or team-based security environments.
✅ Custom Sensitivity Tuning
Users can fine-tune how sensitive the system is to movement, adjusting detection thresholds based on location, time, and risk level.
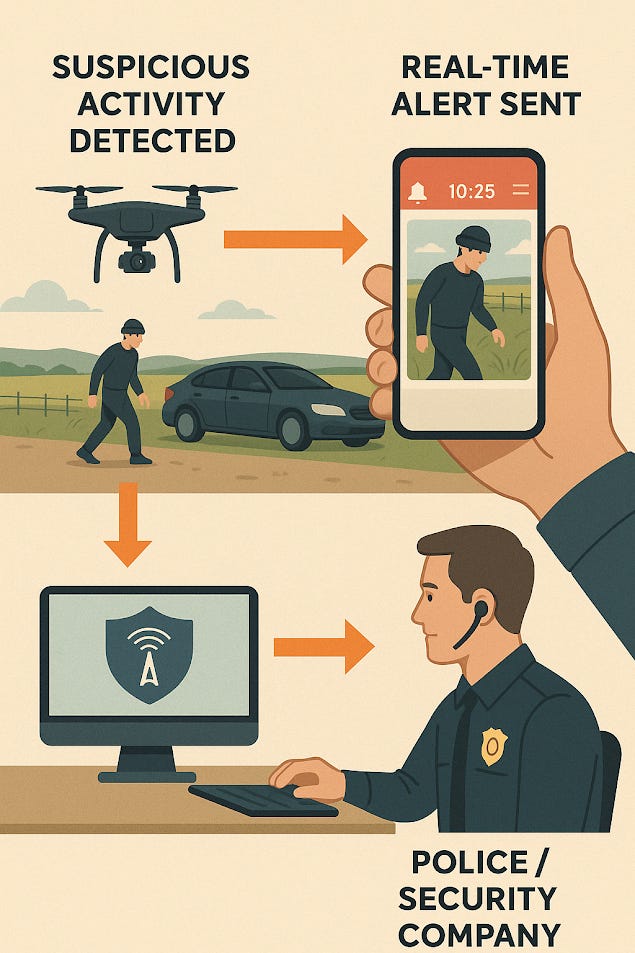
✅ Police/Security Integration
A share button enables the forwarding of alerts, video, and metadata to law enforcement or private security — including the option for real-time streaming if needed.
✅ Drone Surveillance Ready
Supports integration with drones for elevated or mobile monitoring — ideal for large perimeters, fields, rooftops, or difficult terrain.
✅ Facial Recognition & Anti-Mask Detection
Smart facial recognition differentiates between known and unknown individuals. The system can even flag when suspicious face masks (such as silicone replicas) may be used to impersonate someone.
✅ AI-Powered Behavior Analysis
With AI models that continue to learn over time, the system can distinguish between regular and irregular activity — reducing false positives while improving detection accuracy.
Applications:
Vehicle Protection: Detects individuals loitering around or attempting to access your car, motorcycle, or delivery van — even in underground or remote parking.
Home Security: Monitors entrances, windows, and backyards for unexpected motion, package theft, or attempted break-ins.
Commercial & Office Buildings: Protects properties after hours and alerts security staff or management instantly.
Public Space Surveillance: Ideal for municipalities and organizations monitoring public areas or transportation hubs.
High-Risk Zone Monitoring: Can be deployed in sensitive areas to detect suspicious packages or unauthorized activity.
Future Expansion Possibilities:
Voice-Activated Interaction & Alert Playback
Thermal or Night Vision Support
Integration with Smart Locks & Lighting Systems
Crowd Monitoring & Anomaly Detection in Public Events
Global Alert Dashboard for Enterprise Users
Conclusion:
This smart security software concept represents a forward-thinking approach to personal and environmental safety. By combining motion detection, facial recognition, AI learning, and live notification systems — including direct contact with law enforcement — it creates a proactive layer of defense for both individuals and institutions.
As security concerns continue to grow worldwide, tools like these can become vital guardians of our everyday lives — watching quietly in the background and responding in an instant when something’s not right.
Smart Security Software That Detects Suspicious Movements and Sends Real-Time Alerts
Created on: 2024-12-10 17:22
Published on: 2024-12-10 17:23
In an age where safety is a growing concern for individuals, families, and organizations, advanced surveillance technologies are becoming essential. This new concept introduces a smart security software solution capable of detecting suspicious movements near vehicles, homes, and specific areas using connected cameras. It sends real-time alerts to users, complete with video or image snapshots, to help prevent theft, unauthorized access, and even the planting of dangerous devices.
The system is designed to operate seamlessly with various types of cameras — including fixed, mobile, and drone-mounted — offering flexible and reliable protection. By leveraging artificial intelligence, real-time communication, and customizable detection levels, it provides a comprehensive safety net for both private and public use.
Key Features and Capabilities
🔔 Real-Time Alerts with Media
As soon as unusual movement or activity is detected, the software captures a short video or still image and sends it as an alert to users. This immediate feedback empowers users to respond quickly and effectively.
👥 Multi-User Parallel Notifications
The system can notify multiple users simultaneously, allowing families, colleagues, or security teams to remain informed and act as needed, even from different locations.
🎛️ Custom Sensitivity Levels
Users can control how sensitive the detection system is, adjusting thresholds for specific environments or hours of the day. This helps avoid false alarms while ensuring real threats are recognized immediately.
🚨 Direct Security Response Options
The software offers an option for users to contact police or private security forces in real time. Alerts, media, and live feeds can be shared with authorities at the tap of a button.
🤖 AI-Enhanced Detection (When Available)
Where possible, the system uses artificial intelligence to assess behavior patterns and recognize anomalies — distinguishing between normal activity and potential threats.
🏠🚗🌐 Multi-Purpose Deployment
Whether it’s monitoring your car, securing your home, or guarding a commercial or open-air facility, the software adapts to a wide range of use cases.
🚁 Drone Camera Support
The system is compatible with drone-based surveillance, allowing for real-time aerial monitoring of large or complex areas that are difficult to monitor with stationary cameras.
🧠 Facial Recognition & Mask Detection
The software can identify familiar faces and authorized individuals. It can also raise an alert if it detects suspected attempts to bypass facial recognition using hyper-realistic silicone masks — an emerging threat in high-security scenarios.
⚠️ Camera Status Monitoring
The system doesn’t just monitor external threats — it also protects itself. If a camera is blocked, damaged, or disconnected, users are instantly informed, ensuring that the surveillance network remains intact and functional.
Use Cases
Vehicle Surveillance: Protect cars, delivery vans, or motorcycles from break-ins or vandalism in driveways, garages, or parking lots.
Residential Security: Monitor entrances, windows, and gardens to detect trespassers or package theft.
Business & Office Use: Protect storefronts, warehouses, and offices during off-hours or in high-traffic zones.
Public and Remote Spaces: Monitor public areas, construction sites, or rural properties with drone support or mobile units.
Future Potential
The software can be expanded to integrate with other smart technologies and platforms, such as:
Smart locks, alarms, and lighting systems
Voice assistants and smart home hubs
Law enforcement communication networks
Thermal and night vision enhancements
Enterprise-level dashboards for large-scale surveillance
Conclusion
This smart security software represents a powerful evolution in personal and environmental safety. With its ability to monitor, analyze, and respond to potential threats in real time, it offers a proactive solution in a world where reacting too late is no longer an option.
Its AI-enhanced capabilities, multi-device integration, drone compatibility, and facial recognition support make it an adaptable and intelligent tool for protecting people, property, and peace of mind.
Whether you're securing your home, monitoring your business, or protecting a public space, this system has the potential to be a reliable partner in safety.
Note: This is a conceptual product idea. Additional research is recommended to confirm whether similar systems currently exist in the market.
Let me know if you'd like thiOf course! Here’s an extended continuation of the article, diving deeper into technical details, ethical considerations, customization options, and global market relevance, giving it more substance for publication or pitching to investors or institutions.
Technical Architecture & System Design
The proposed security software leverages a modular architecture built around several key components:
1. Motion Analysis Engine
This core module analyzes live video feeds using advanced computer vision techniques to detect irregular motion patterns. It can differentiate between routine movements (like passing vehicles or pets) and high-risk behaviors (such as loitering, fast approach, or object placement near the target).
2. AI-Based Recognition Layer
Using AI algorithms and machine learning, the software can learn from past events to improve detection accuracy. The AI layer enables:
Human vs. Object recognition
Behavior prediction (based on posture, speed, and gesture)
Mask and disguise detection
Facial recognition for approved users
3. Alert Engine
Once a threat is identified, this module instantly creates and pushes a notification package to the user's device. Each package includes:
A time-stamped video or still image
Type of threat or anomaly detected
A shareable link for security teams or authorities
Optional livestream access
4. Fail-Safe Monitoring
To ensure reliability, the system constantly audits its own network:
Alerts if a camera is blocked, covered, or physically damaged
Reports outages or connectivity problems
Can switch to backup drone or mobile surveillance if enabled
5. User Dashboard & Settings
Users control the system via a mobile app or desktop interface, with access to:
Live feeds and archives
Threat level configuration
Alert routing (who gets notified and when)
Permissions for facial recognition database
Emergency contact linking (security companies, police, neighbors)
Ethical Considerations & Privacy
While this software enhances safety, it must also uphold strict ethical standards. Responsible use includes:
Data Protection: All video and recognition data should be encrypted and stored securely, with options for local-only storage if preferred.
Consent-Based Recognition: Facial recognition databases should be opt-in, with transparent logs of recognized entries and manual approval of changes.
Private Zones: Users should be able to mask out private areas from detection, like neighbors' windows, to avoid surveillance overreach.
Transparency & Accountability: Every alert and interaction with the system should be logged for future review, useful both for users and law enforcement.
Customization for Different Users
This security system is not one-size-fits-all — it can be tailored for various sectors:
User TypeCustom FeaturesHomeownersPet-friendly zones, face recognition of family, package theft alertsVehicle OwnersParking lot motion alerts, anti-vandalism detection, car camera integrationRetail & OfficesAfter-hours monitoring, access control, multi-user coordinationWarehouses & FactoriesPerimeter drones, smart gates, equipment tampering detectionPublic InstitutionsCrowd monitoring, emergency escalation workflows, AI event classification
Global Market Relevance
This concept addresses rising global concerns:
Urban Crime: Theft, break-ins, and tampering are increasing in dense urban zones.
Terror & Vandalism: Monitoring for planted devices or sabotage is relevant for embassies, transport hubs, and public institutions.
Remote Property Protection: Drones and remote cameras secure rural homes, farms, or vacation homes.
AI Adoption in Security: Governments and companies are increasingly looking to AI for smarter, non-intrusive surveillance tools.
The system could also be adapted for:
Smart cities
Schools and campuses
Airports and railway stations
Military installations
VIP security and convoy support
Vision for the Future
With further development, the software could evolve into a full ecosystem, incorporating:
AR Glasses for security guards linked to alerts
Smart Lockdown Protocols (locking doors/windows based on threat level)
Cross-Device Sync between cars, homes, and public locations
Neighborhood Watch Networks (linking houses in the same area)
Closing Thoughts
This next-gen security software has the potential to revolutionize the way individuals and organizations protect themselves. With smart detection, real-time communication, and deep customization, it bridges the gap between traditional surveillance and proactive intervention.
By combining cutting-edge technology with user-centric design and ethical foresight, this concept is not just about watching — it's about responding, preventing, and protecting.
Note: This article describes a conceptual innovation. The author recommends exploring technical feasibility, legal compliance, and potential market competitors before moving toward production.
Here's a refined and comprehensive version of your article that includes sound detection and is structured for publication or presentation. This unifies all your input while preserving detail, clarity, and flow:
Smart Security Software That Detects Suspicious Movements, Sounds, and Sends Real-Time Alerts
In an age where security threats can arise unexpectedly, technology must evolve beyond passive surveillance. This smart security software concept is a next-generation solution that not only detects suspicious movements near vehicles, homes, or secured areas but also analyzes sound patterns to identify threats — all while delivering instant alerts with visual and audio evidence to users in real time.
🔒 What It Does
This system leverages AI-powered analysis of video and sound feeds to detect:
Suspicious loitering or unauthorized motion
Sounds such as glass breaking, aggressive shouting, gunshots, explosions, or attempted tampering
Camera health issues (e.g., being covered, destroyed, or disconnected)
Alerts — complete with video, audio, or image clips — are sent to users and/or security responders the moment a threat is detected.
🔑 Key Capabilities
✅ Real-Time Alert System
The system sends time-stamped notifications with video, audio, or still images directly to users — allowing immediate action.
✅ Sound Recognition
It detects high-risk audio patterns such as:
Glass breaking
Forced entry or impacts
Screams or threats
Gunshots, explosions, or device tampering
Using machine learning, it filters out irrelevant noise and adapts over time.
✅ Multi-User Notification
Multiple people (e.g., family members, security teams) receive parallel alerts across devices.
✅ Adjustable Detection Sensitivity
Users can customize motion and sound sensitivity levels for different locations, times, or threat levels — reducing false alarms.
✅ Facial Recognition & Mask Detection
Recognizes authorized users, while flagging unfamiliar faces or hyper-realistic masks used to evade identification.
✅ Camera & Device Health Monitoring
Monitors connected devices and sends alerts if:
A camera is physically damaged, covered, or tilted
A connection is lost unexpectedly
✅ Police/Security Sharing Option
With one tap, users can forward media and data to law enforcement or private security — or enable live streaming for rapid response.
✅ Drone Camera Support
Compatible with drone-based surveillance for covering large or complex spaces like rooftops, open fields, or facility perimeters.
🔍 How It Works
The system connects with fixed, mobile, or aerial cameras and microphones. It runs continuously, analyzing real-time input for:
Abnormal behavior
Intrusion attempts
Irregular audio patterns
When an anomaly is detected, it:
Captures high-quality video/audio.
Sends alerts to configured devices.
Provides sharing and escalation options for fast action.
🧠 Powered by AI
AI integration enables:
Smart object recognition (distinguishing people from animals or shadows)
Behavior analysis (e.g., loitering, crouching, approaching vehicles)
Audio classification (e.g., explosion vs. engine noise)
Learning and adaptation over time for better accuracy
🔧 Technical Architecture
ModuleFunctionMotion & Sound Detection EngineAnalyzes video/audio for abnormal eventsAI Behavior & Audio ClassifierRecognizes movement types, sound types, and threat levelsAlert EngineSends multimedia alerts to user devicesFail-Safe MonitorDetects device failure, camera disconnection, tamperingDashboard/App InterfaceUser control panel for live feeds, settings, and logs
📌 Use Cases
Vehicle Protection: Detects break-in attempts, loiterers, or impact sounds.
Home Security: Identifies unwanted presence, package theft, or glass breakage.
Office/Storefront Monitoring: After-hours alerts, sound-triggered surveillance.
Public Areas: Detects aggressive behavior, vandalism, or potential threats.
Remote Properties: Monitors rural homes or construction sites with drone access.
🌐 Customization for Users
UserCustom FeaturesHomeownersPet-safe zones, package theft detectionDriversCar alert zones, trunk/sensor tamperingSecurity TeamsMulti-camera feeds, escalation toolsBusinessesAfter-hours intrusion detection, facial recognition logsPublic AgenciesCrowd detection, bomb-threat surveillance, AI triage
🌍 Global Relevance & Future Vision
This system is aligned with:
Urban crime prevention
Smart city infrastructure
Public transport hub security
Rural and remote location protection
Future Add-Ons May Include:
Voice command activation
Thermal/night vision compatibility
Integration with smart lights, locks, alarms
Crowd behavior analysis
Enterprise dashboard for multi-location monitoring
⚖️ Privacy & Ethics
Encrypted storage and secure cloud access
User-controlled recognition databases
Private area masking for ethical compliance
Transparent logs for every alert and data access
🔚 Conclusion
This smart security software represents a proactive leap forward in personal, commercial, and public safety. With motion and sound detection, real-time response tools, and AI learning, it serves as a digital guardian that watches quietly — and reacts instantly when something’s not right.
As threats evolve, so must our defenses. This concept reflects the future of integrated, intelligent, and intuitive protection systems.
Note: This article describes a conceptual system. Research is advised to determine if similar commercial products already exist.
Here is your technical article version of the smart security software concept, written in a structured, professional format for industry stakeholders, technical teams, or publication in a journal or whitepaper setting:
Smart Security Software for Real-Time Detection of Suspicious Movements and Sounds
Author: [Name/Org Placeholder]
Published on LinkedIn: December 10, 2024
Version: Conceptual Technical Overview
Abstract
Modern security demands proactive, intelligent systems capable of real-time analysis and intervention. This article presents a conceptual framework for a smart security software solution designed to detect both suspicious movements and anomalous sound patterns, delivering immediate multimedia alerts and offering integration with external security forces. It supports facial recognition, drone surveillance, customizable sensitivity thresholds, and operates across residential, vehicular, and commercial environments.
1. Introduction
With the rise in property crime, public disturbances, and high-risk intrusion scenarios, conventional passive surveillance is no longer sufficient. This proposed system combines motion tracking, audio recognition, and artificial intelligence (AI) to detect, assess, and escalate threats in real time.
Its versatility allows it to be applied in multiple domains, including:
Private residences and vehicles
Commercial and industrial properties
Public infrastructure and high-risk zones
2. System Architecture
2.1 Core Components
ModuleDescriptionMotion Analysis EngineUses computer vision to identify non-routine movements (e.g., loitering, forced entry).Sound Detection ModuleAnalyzes real-time audio for specific patterns (gunshots, shouting, glass breaking, explosions).AI Recognition LayerApplies machine learning for object/person identification and behavior prediction.Alert & Notification EngineDelivers real-time alerts with video/image/audio payloads to connected users or services.Camera Health MonitoringDetects and reports offline, obstructed, or tampered surveillance feeds.Drone Interface ModuleEnables surveillance using aerial devices for expanded field of view.
3. Functional Capabilities
3.1 Real-Time Alerts
Multimedia payload (video/image/audio) delivered instantly to designated recipients
Timestamped threat logs with classification metadata
3.2 Multi-Channel Notifications
Alerts sent in parallel to multiple users/devices
Ideal for households, security teams, or multi-role organizations
3.3 Configurable Sensitivity
User-defined detection thresholds
Time-of-day profiles and region-based tuning
Adjustable AI aggressiveness to reduce false positives
3.4 Law Enforcement Integration
“Share Now” functionality for rapid escalation
Live-stream capabilities upon trigger events
3.5 Facial Recognition & Anti-Mask Detection
Recognizes pre-authorized individuals
Flags hyper-realistic silicone masks and disguise attempts using thermal and pattern deviation models
3.6 Sound Pattern Detection
Pretrained and custom-trainable classifiers for detecting:
Explosions
Gunshots
Screaming/shouting
Tampering noises
Glass breakage
Machine learning adaptation based on environment and incident history
4. Security and Reliability
End-to-end encryption for data at rest and in transit
Audit trail logging for every alert and system interaction
Local and cloud failover architecture
Automatic drone fallback surveillance if ground cameras are compromised
5. Use Case Matrix
Use CaseFeatures EmployedVehicle SurveillanceMotion detection, audio alerts, face recognition, camera health alertsResidential SecurityLoitering detection, glass break recognition, multi-user alertsBusiness/Industrial SecurityAfter-hours monitoring, team coordination, remote area coveragePublic Space SurveillanceCrowd behavior analysis, drone support, anomaly flaggingHigh-Risk ZonesPackage detection, anti-tamper alerts, security force escalation
6. Ethical and Privacy Considerations
Data Ownership: Users control access, storage, and deletion preferences.
Consent-Driven Recognition: Opt-in databases and identifiable logs ensure ethical use of biometric data.
Zone Masking: Ability to exclude non-monitored regions (e.g., neighboring properties) from surveillance.
Transparency: All interactions with alerts are recorded and reviewable by users and authorities.
7. Future Extensions
Voice-triggered emergency interactions
Smart lock and lighting system integrations
Thermal/Night vision enhancement compatibility
Crowd density monitoring for public events
Central dashboard for enterprise/multi-site operations
8. Conclusion
This conceptual smart security software represents a new tier of proactive threat detection—integrating motion, sound, AI, and multi-user communication into a seamless system. By providing real-time intelligence and rapid escalation options, it transforms surveillance from a passive record-keeping tool into an active safety solution.
Disclaimer: This system is presented as a conceptual design. Further technical validation, prototyping, and competitive analysis are recommended prior to development or deployment.
Here is a second version of the scholarly article, with a slightly different structure and more concise academic tone. This version emphasizes system functionality, interdisciplinary relevance, and potential for applied research or prototyping:
A Conceptual Framework for Intelligent Surveillance Software Integrating Motion and Sound-Based Threat Detection
Abstract
The development of proactive surveillance systems is critical in addressing contemporary security challenges across private, commercial, and public domains. This paper outlines the design of a conceptual software platform that integrates real-time video and audio analysis for the detection of suspicious activity. Utilizing artificial intelligence and machine learning, the system identifies anomalies in movement and sound, supports facial recognition, monitors system health, and enables user notifications and escalation through an adaptive multi-user interface. This framework offers a foundation for intelligent, responsive, and ethically conscious surveillance solutions.
1. Introduction
Traditional security solutions typically involve static video recording and require human interpretation. These systems, while useful for retrospective review, are insufficient for immediate incident prevention. Recent advances in artificial intelligence, acoustic analysis, and edge computing provide new opportunities for developing autonomous security platforms capable of recognizing and reacting to threats in real time.
The proposed system addresses the need for dynamic threat detection by incorporating visual and acoustic event recognition, real-time alerts, and user-initiated escalation options. It is designed to operate in diverse environments including private homes, vehicles, corporate properties, and sensitive public infrastructure.
2. System Overview
The system combines visual and auditory monitoring using a modular software architecture. It operates with fixed, mobile, or aerial (drone-based) camera systems and supports cloud or edge-based processing.
2.1 Components
Motion Detection Engine: Detects and classifies movement patterns (e.g., loitering, fast approach, forced entry).
Acoustic Analysis Module: Recognizes specific audio events such as explosions, shouting, glass breaking, and tampering.
Machine Learning Layer: Supports behavior modeling and adaptive filtering of false positives.
Facial Recognition Subsystem: Identifies approved users and flags anomalies, including the use of deceptive masks.
Alert and Notification Framework: Issues real-time alerts to configured users, including media evidence.
Health Monitoring Agent: Detects tampering, disconnection, or signal loss from cameras and microphones.
3. Functional Capabilities
The system operates continuously and executes the following functions:
Anomaly Detection: Triggers when unusual sound or motion is recorded.
Real-Time Multimedia Alerts: Sends visual or audio snapshots to user devices via secure channels.
Multi-User Access: Allows alerts to be delivered to multiple users simultaneously.
Facial Authentication and Mask Detection: Uses biometric features to differentiate authorized and unauthorized individuals.
Sensitivity Configuration: Enables contextual tuning based on location, time, and risk exposure.
Police/Security Integration: Provides optional links for direct escalation to emergency responders.
4. Application Domains
SectorUse CaseResidentialIntrusion, package theft, motion at entrancesAutomotiveVehicle break-in attempts, perimeter monitoringCommercialAfter-hours activity, restricted area accessPublic SafetySurveillance in parks, transportation hubsRemote InfrastructureMonitoring isolated or critical facilities via drones
5. Ethical and Legal Considerations
Security software with advanced sensory and AI capabilities must address data privacy, surveillance overreach, and consent:
Data Minimization: Only necessary video and audio segments are retained.
User Consent: Facial recognition must be opt-in and compliant with local regulations.
Exclusion Zones: Allows masking of off-limits areas to avoid inadvertent surveillance.
Auditability: Maintains a detailed log of detection events and user/system interactions.
6. Challenges and Future Directions
While conceptually robust, practical implementation faces several challenges:
Contextual Audio Classification: Differentiating between benign and threatening audio events in urban environments.
Edge Processing Limitations: Balancing real-time detection with energy efficiency and bandwidth constraints.
Bias in Recognition Systems: Ensuring equitable performance across demographics and reducing algorithmic bias.
User Interface Design: Delivering actionable alerts without overwhelming users with false positives.
Future research may explore integration with:
Autonomous drones with thermal imaging
AI-enhanced access control systems
Community-shared safety networks
Cloud-based enterprise dashboards for multi-site monitoring
7. Conclusion
This paper proposes a comprehensive model for intelligent security software that unifies motion and sound detection with real-time user interaction. The system’s flexibility, AI capabilities, and scalability make it suitable for deployment in a range of contexts from private homes to public institutions. By shifting from passive recording to active threat recognition and response, such systems represent a crucial advancement in automated security technologies.
Legal & Collaboration Notice
The Smart Security Software for Real-Time Detection of Suspicious Movements and Sounds — including its architecture, AI recognition engine, motion and sound analysis modules, camera health monitoring system, drone surveillance interface, facial recognition and anti-mask detection features, and its multi-user, real-time alert system — is an original invention and publication by Ronen Kolton Yehuda (MKR: Messiah King RKY).
This innovation — encompassing its software framework, detection algorithms, multimedia alert logic, ethical privacy architecture, integration protocols for police and emergency services, and cross-platform ecosystem — was first authored and publicly released to establish intellectual ownership and authorship rights.
All associated technical descriptions, conceptual articles, architectural diagrams, and written texts are part of the inventor’s intellectual property.
Unauthorized reproduction, software engineering replication, or commercial adaptation without written consent is strictly prohibited.
The Smart Security Software introduces a new class of proactive, AI-assisted safety systems that move beyond passive surveillance — combining real-time detection, sound analysis, and immediate response capabilities across residential, vehicular, commercial, and public domains.
It represents a transition from recording incidents to preventing them, uniting human awareness with artificial intelligence for responsible and ethical protection.
I welcome ethical collaboration, licensing discussions, software development partnerships, and investment inquiries for the responsible advancement and global deployment of this innovation.
— Ronen Kolton Yehuda (MKR: Messiah King RKY)